Evilginx is a tool that allows you to create phishing websites capable of stealing credentials and session cookies. It does this by simply proxying HTTP requests between the browser and the targeted site. To the user, it seems like they are using the legitimate website, but little do they know there is a man-in-the-middle. As a result, this style phishing attack even works against 2FA approaches such as TOTP and push notifications.
So, how can you defend against this kind of phishing attack? Security training your users is a good first step, but a phishing domain using a deceptive Unicode character can fool the best of us.
The only way to truly protect your users from this kind of phishing attack is using FIDO.
Attacking Multi-Factor Authentication (MFA) using Evilginx
Let’s take a look at a simple website that has 2FA/MFA enabled. This website asks the user for their username and password before challenging them for their Time-based One-Time Password (TOTP). The user could generate the OTP using an app such as Google Authenticator, a password manager, or even a hardware token.
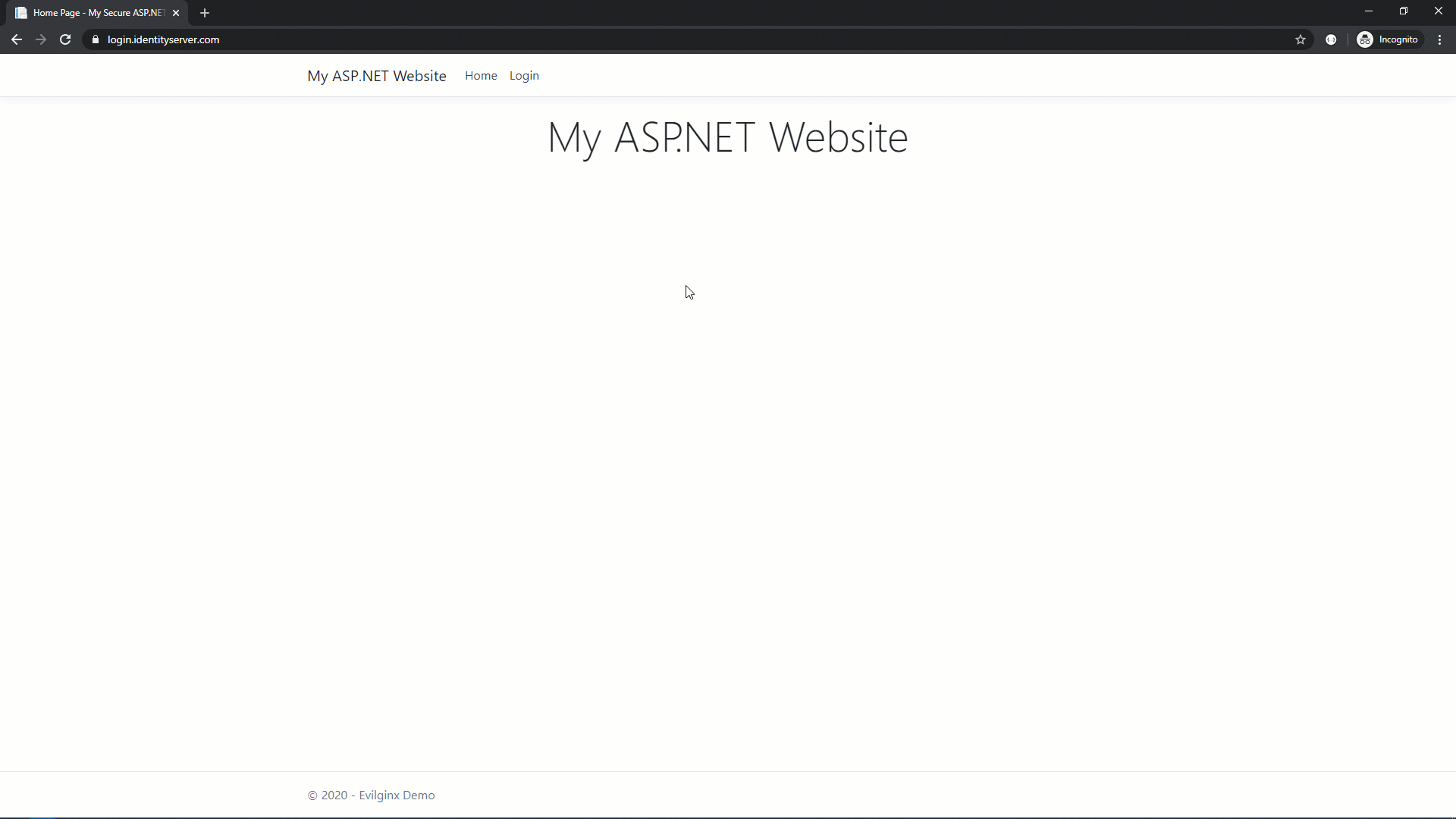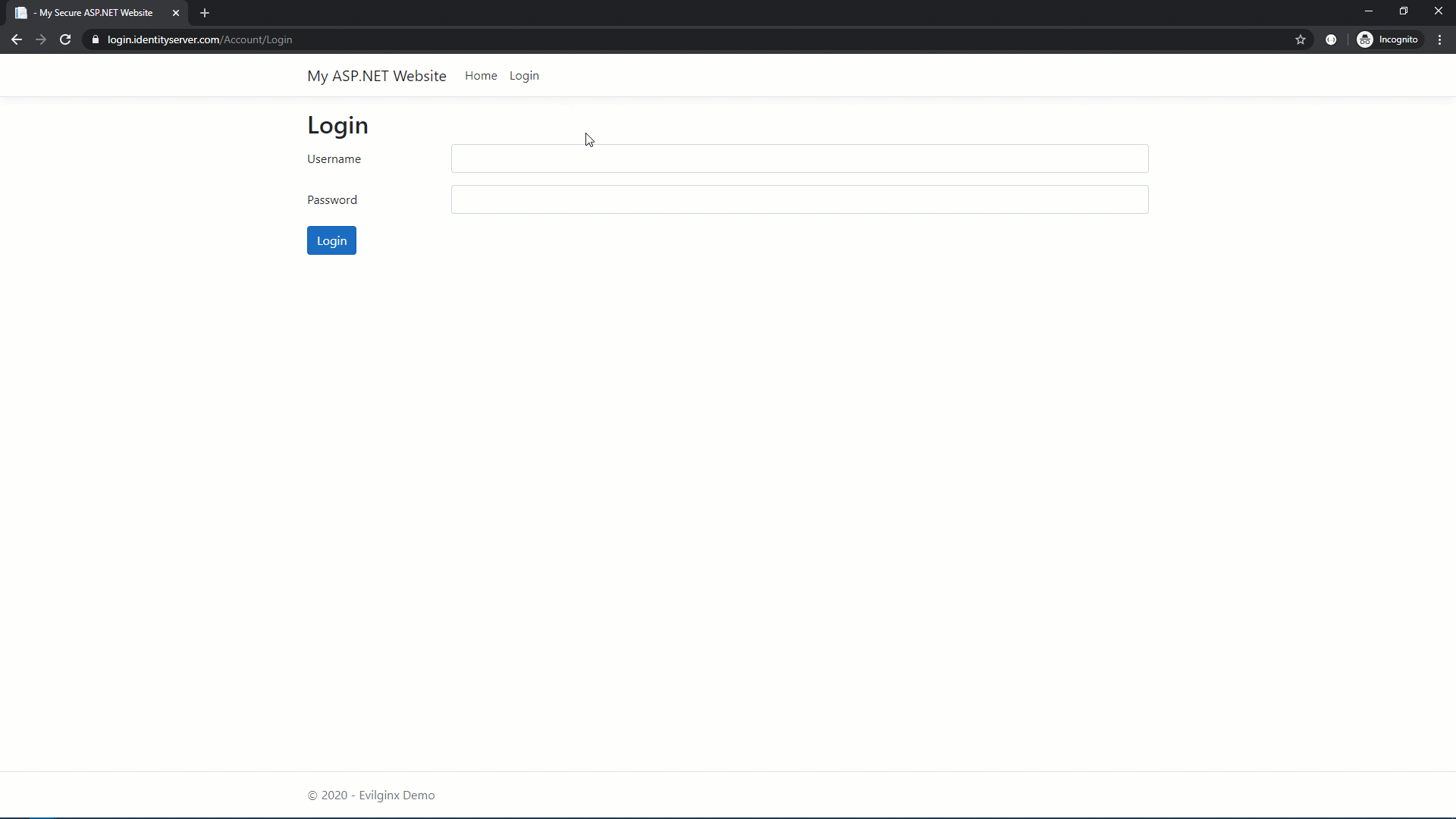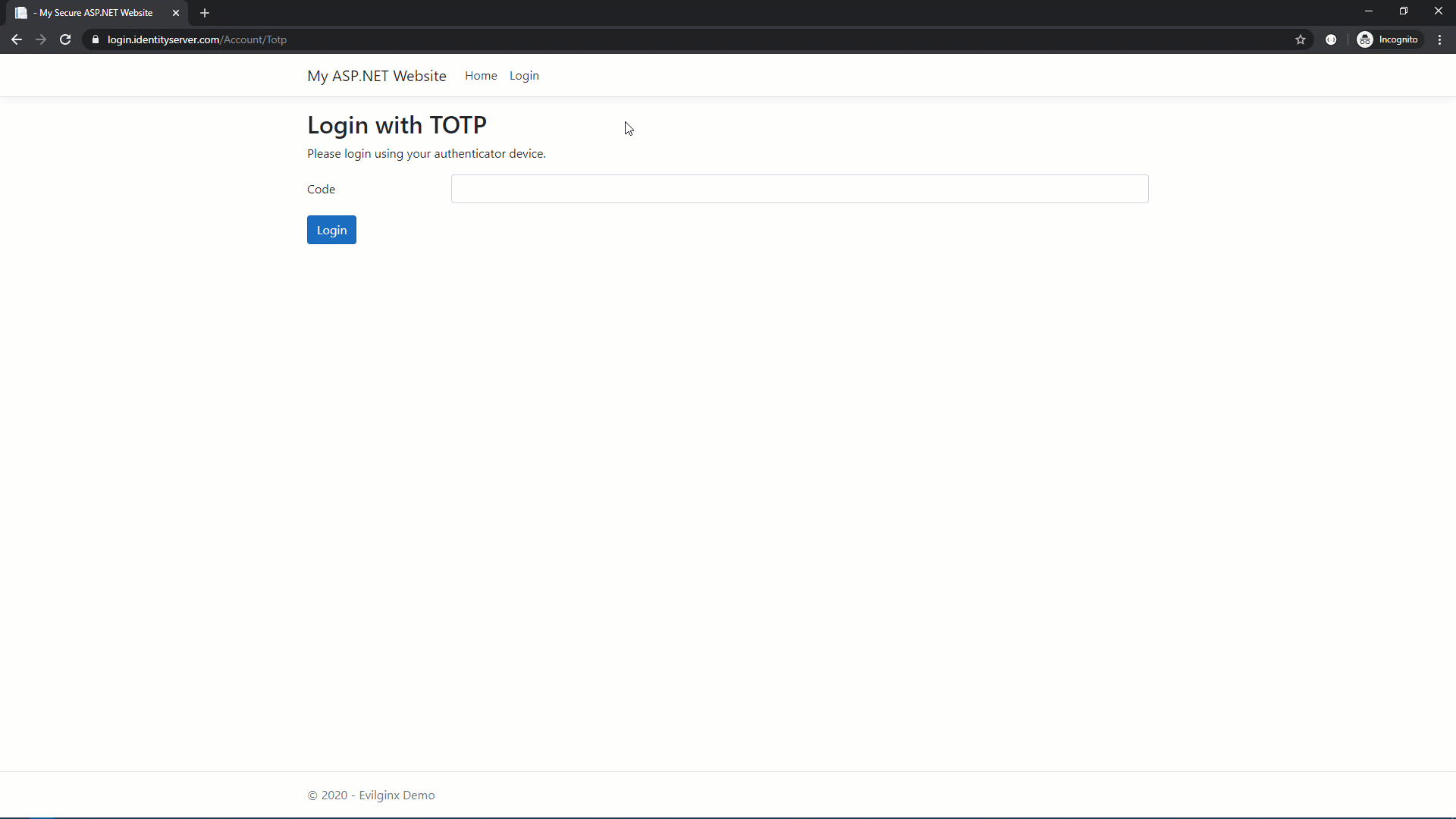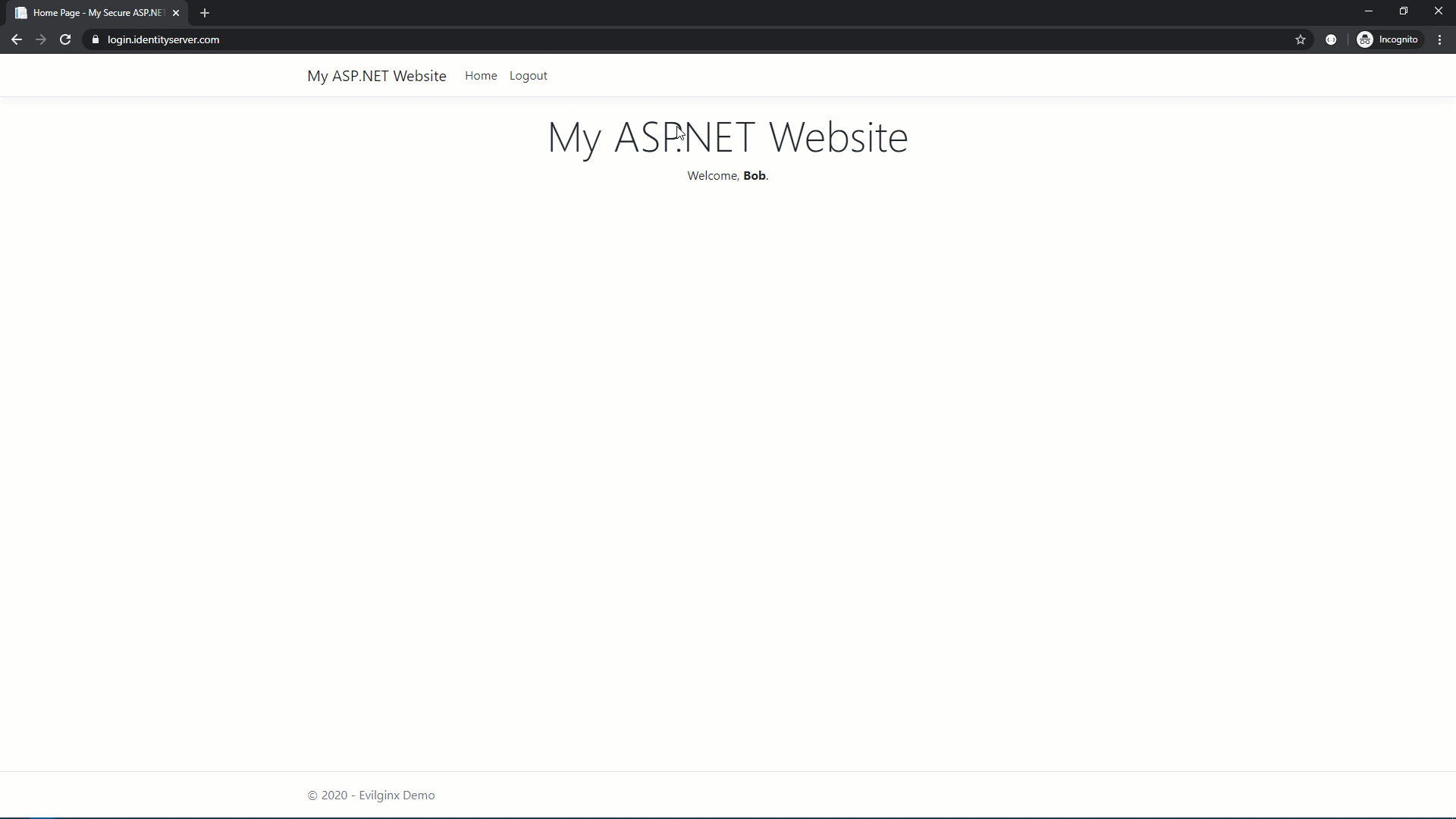
Now, let’s attack that using Evilginx.
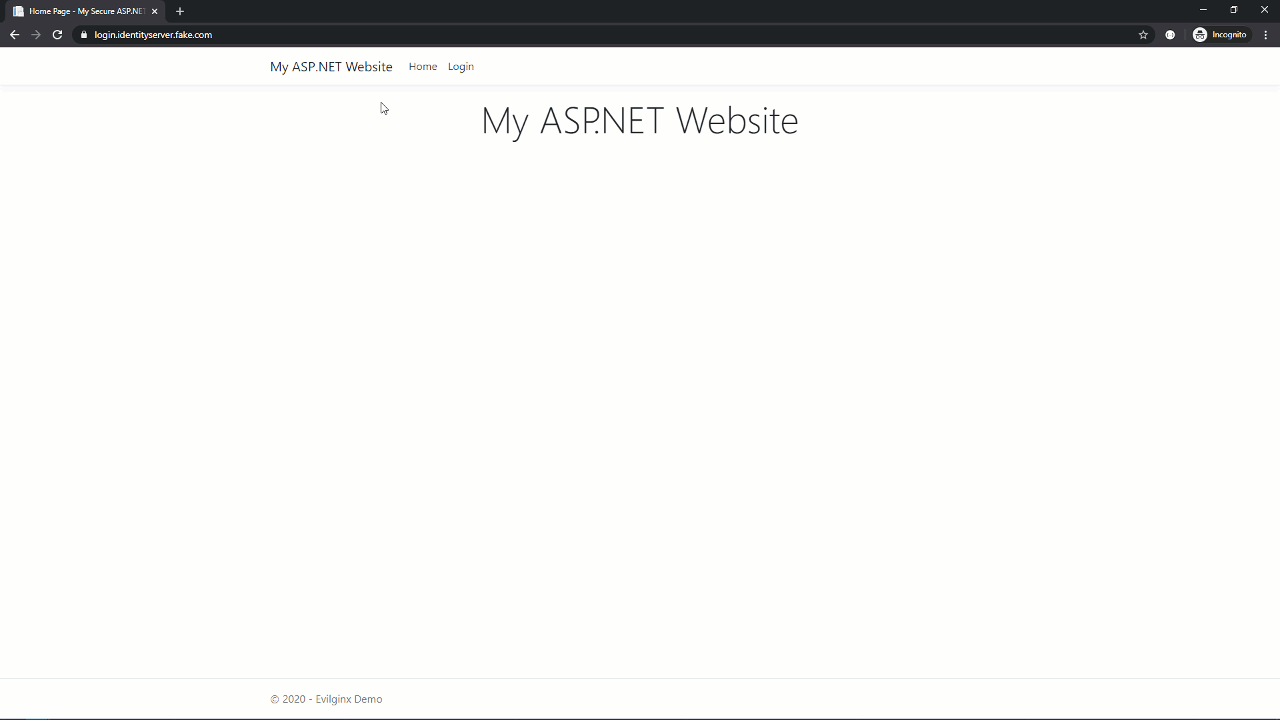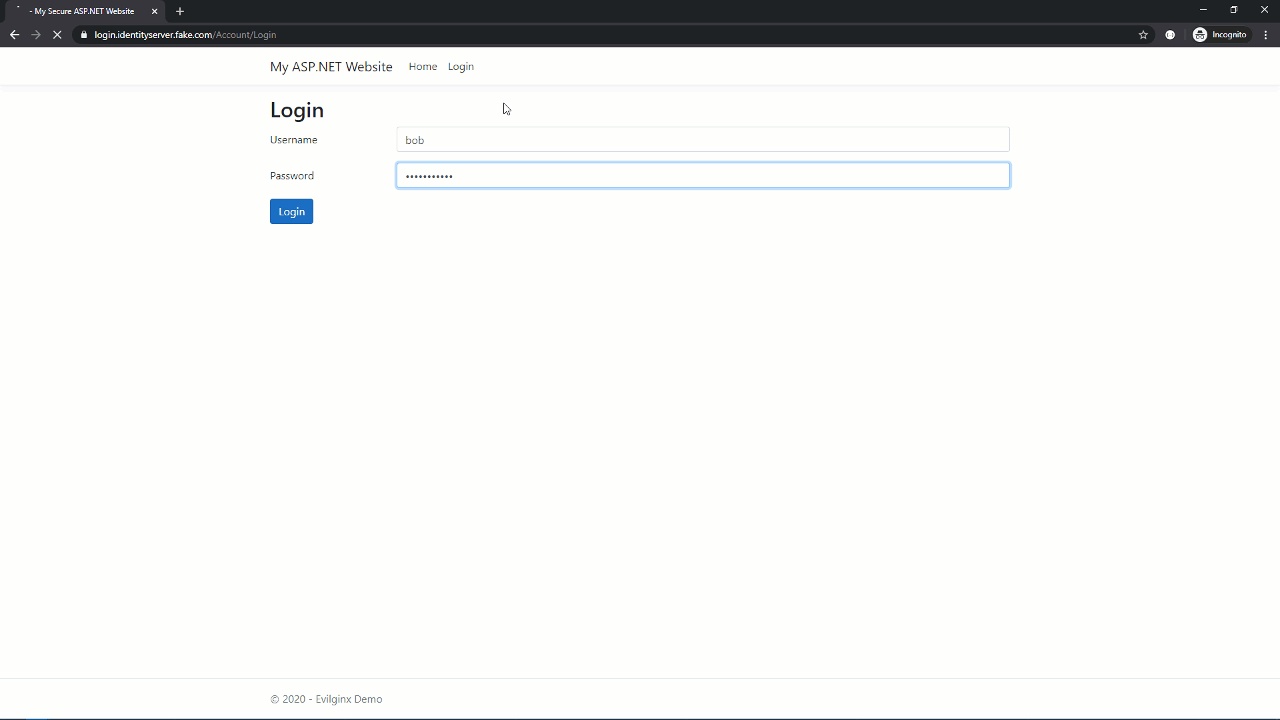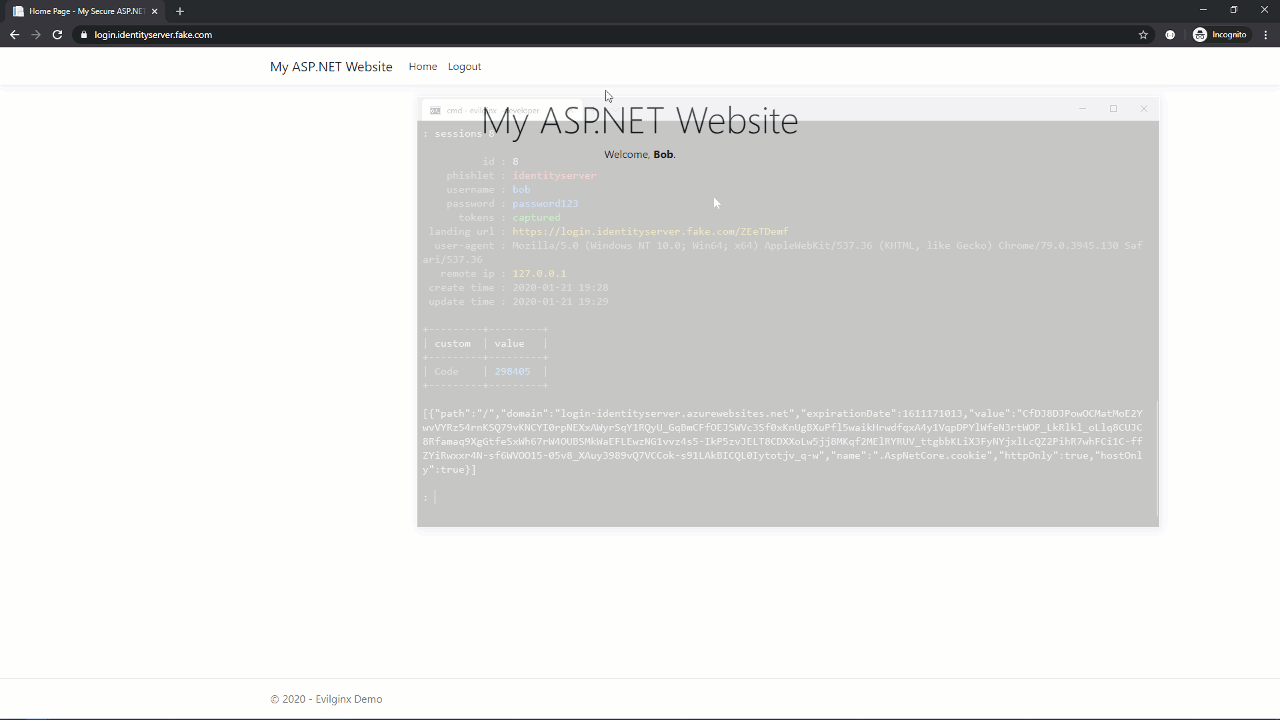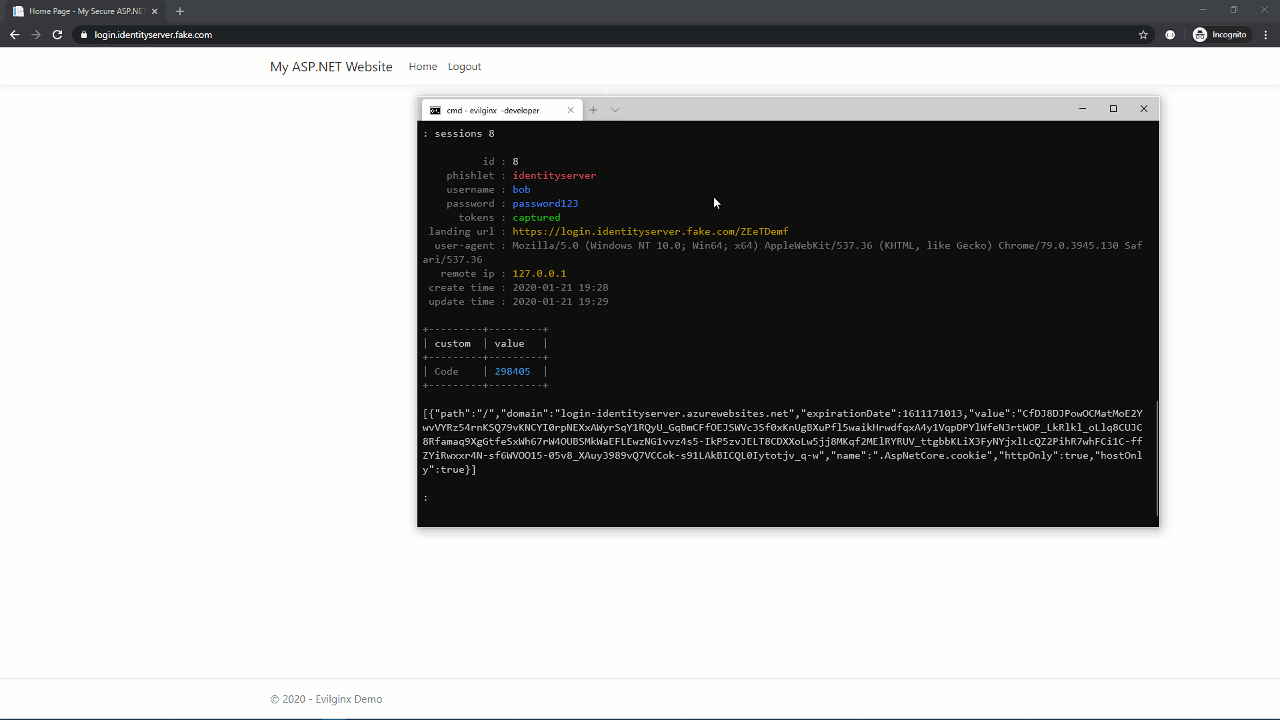
To the user, that looked pretty much the same. The only visible difference was the URL (login.identityserver.com vs. login.identityserver.fake.com). However, in the background, Evilginx stole their credentials and the resulting session cookie. This means the attacker doesn’t need to use the stolen TOTP because they already have what MFA was protecting: an authenticated session.
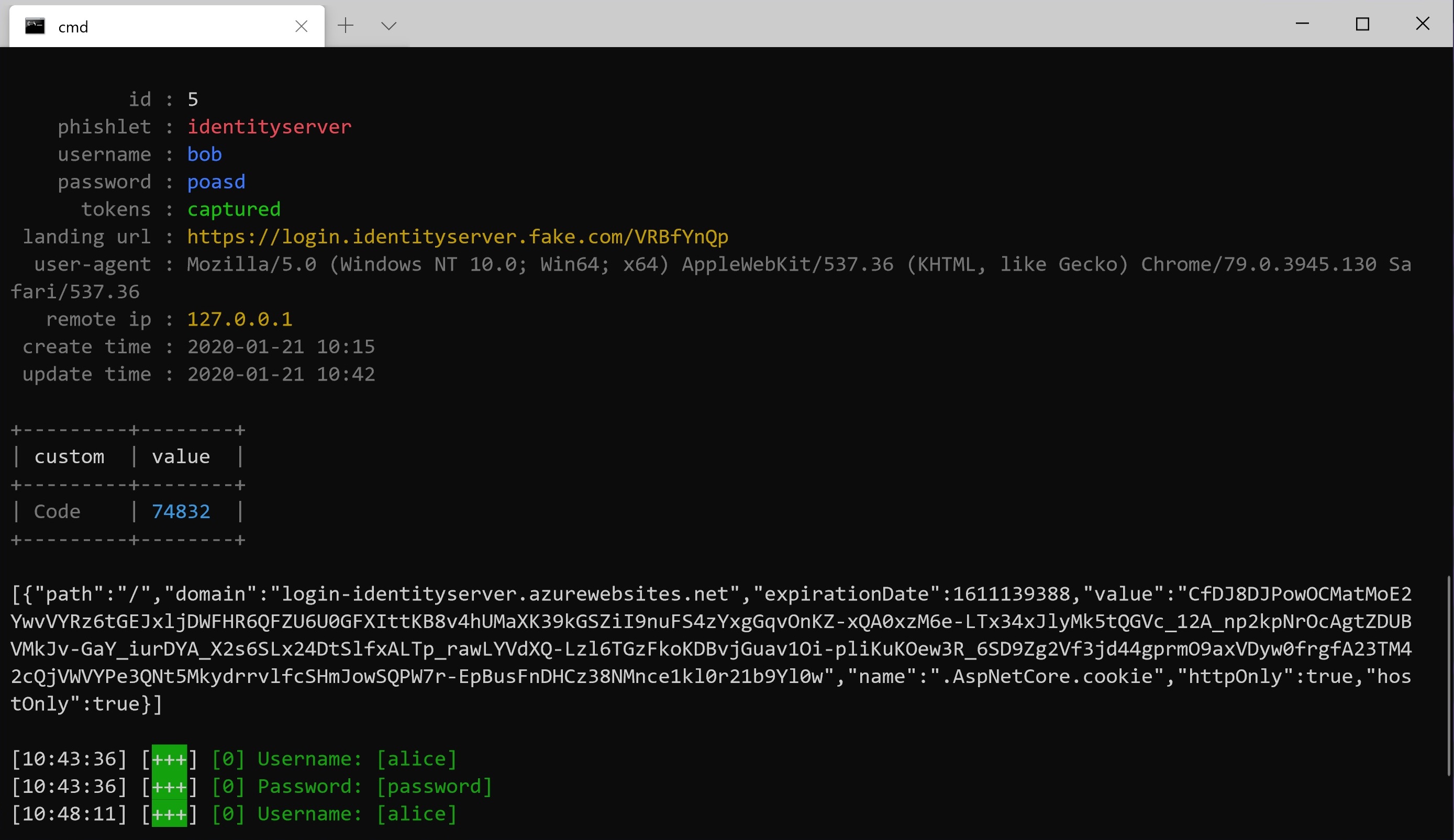
Most authentication methods are susceptible to attack by Evilginx, including SMS OTP, TOTP, proprietary push notifications, and hardware token generators.
Unphishable Multi-Factor Authentication using FIDO2 for ASP.NET
Let’s take a look at the same process, but this time with a user who is using FIDO for their second factor. The user is still using a username and password, but instead of TOTP, they are using their FIDO security key as their second factor. This key doesn’t need to be a physical key; it could be a platform authenticator such as Windows Hello.
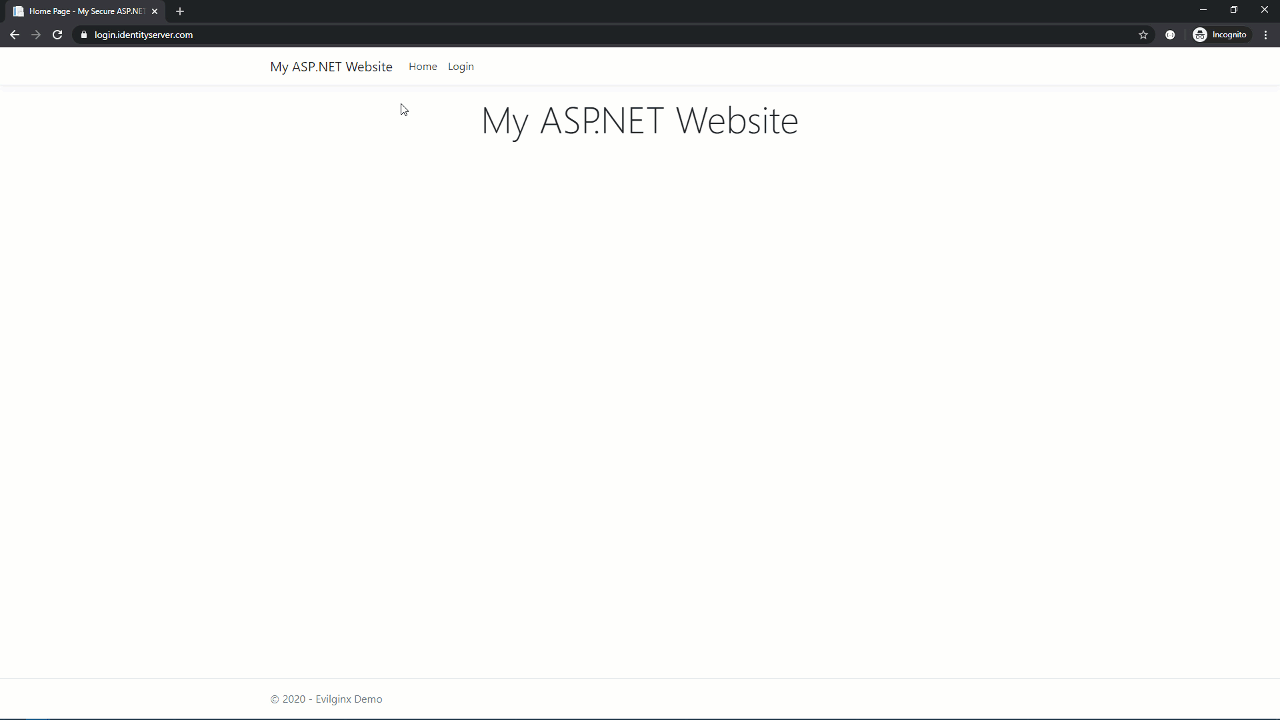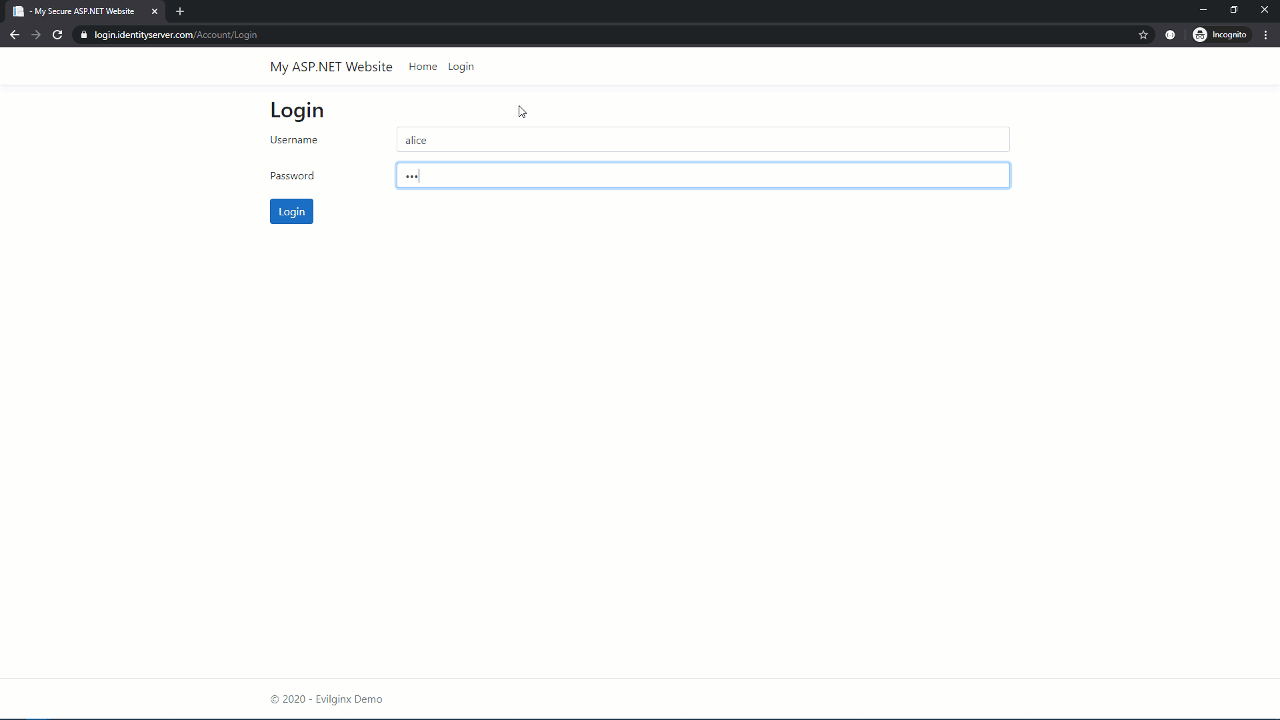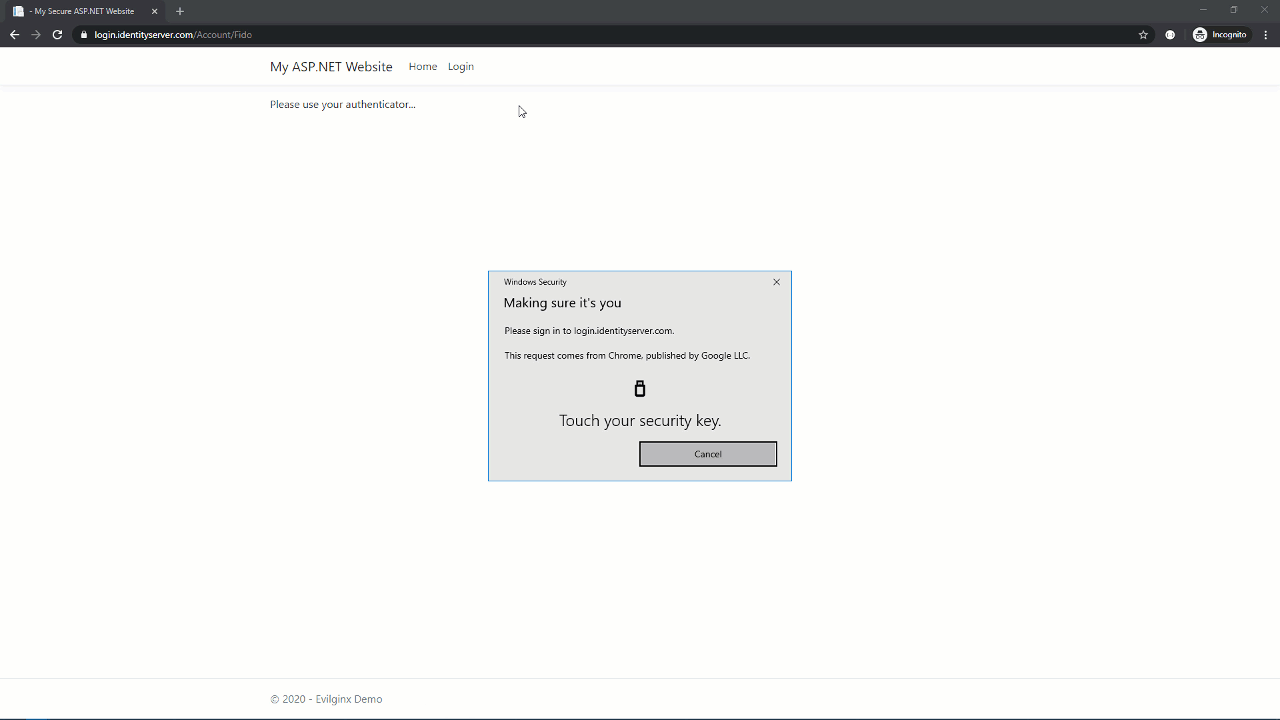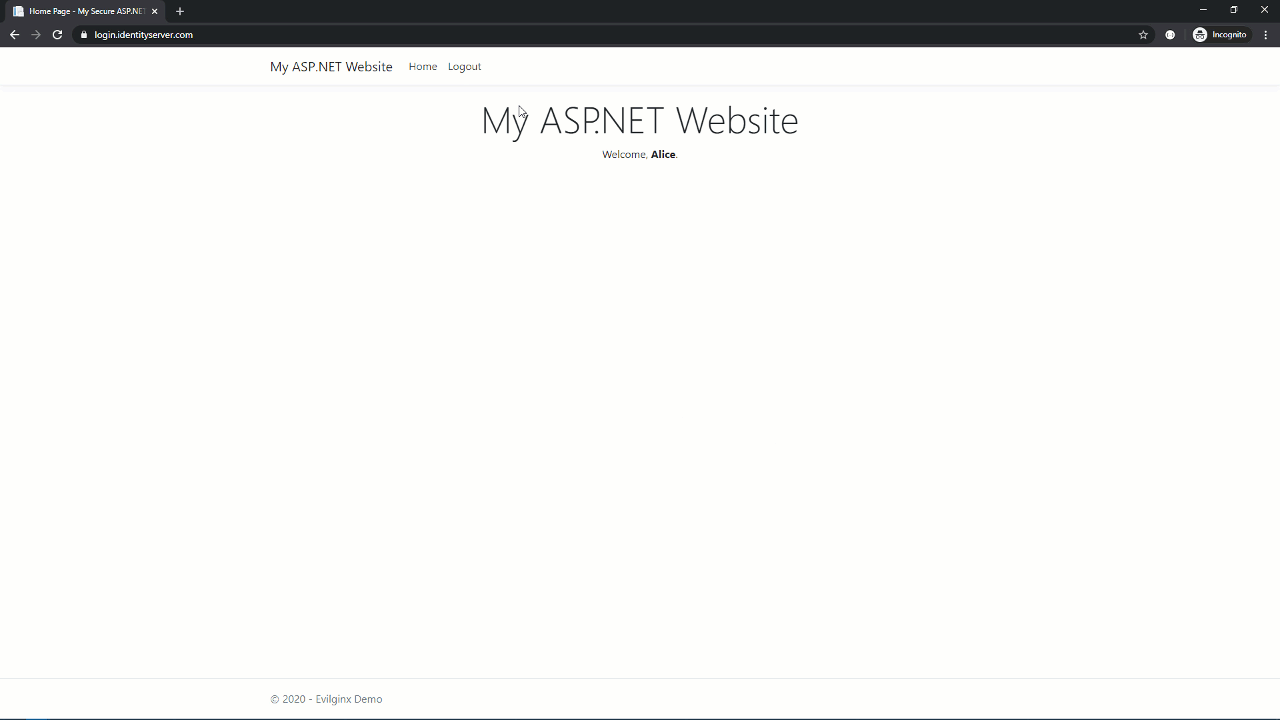
Now, let’s see the same process in our Evilginx phishing site.
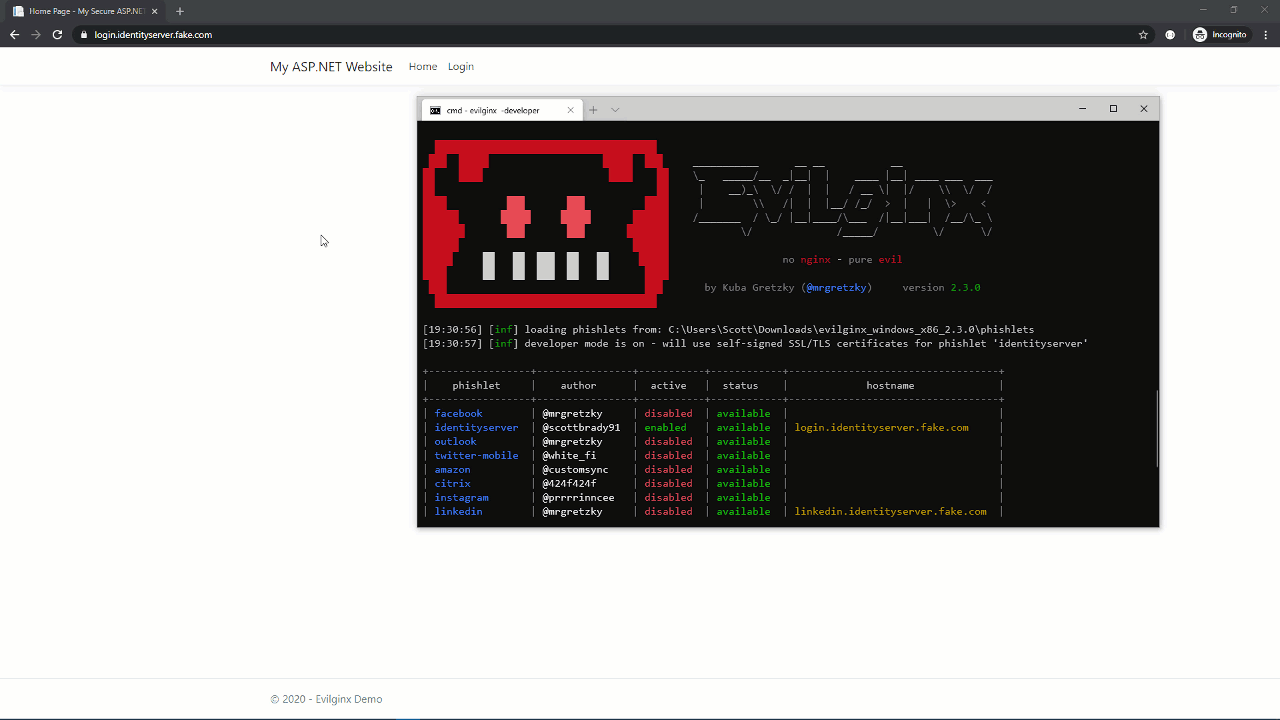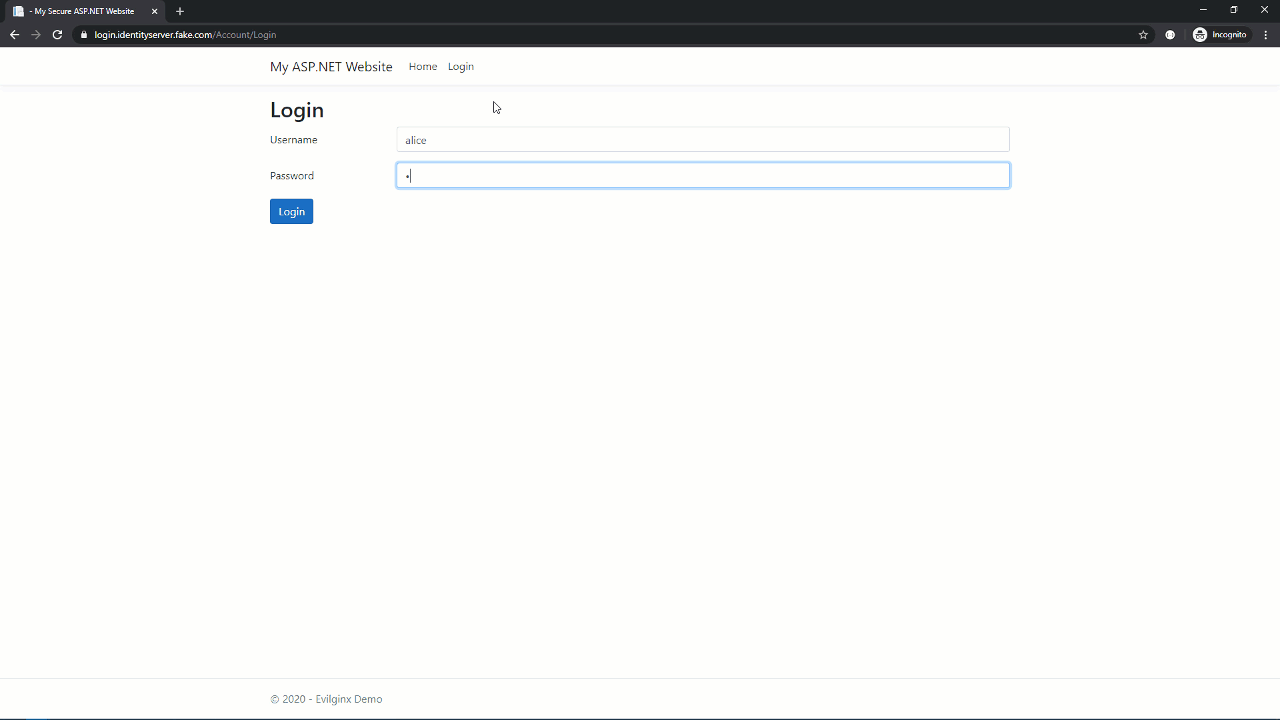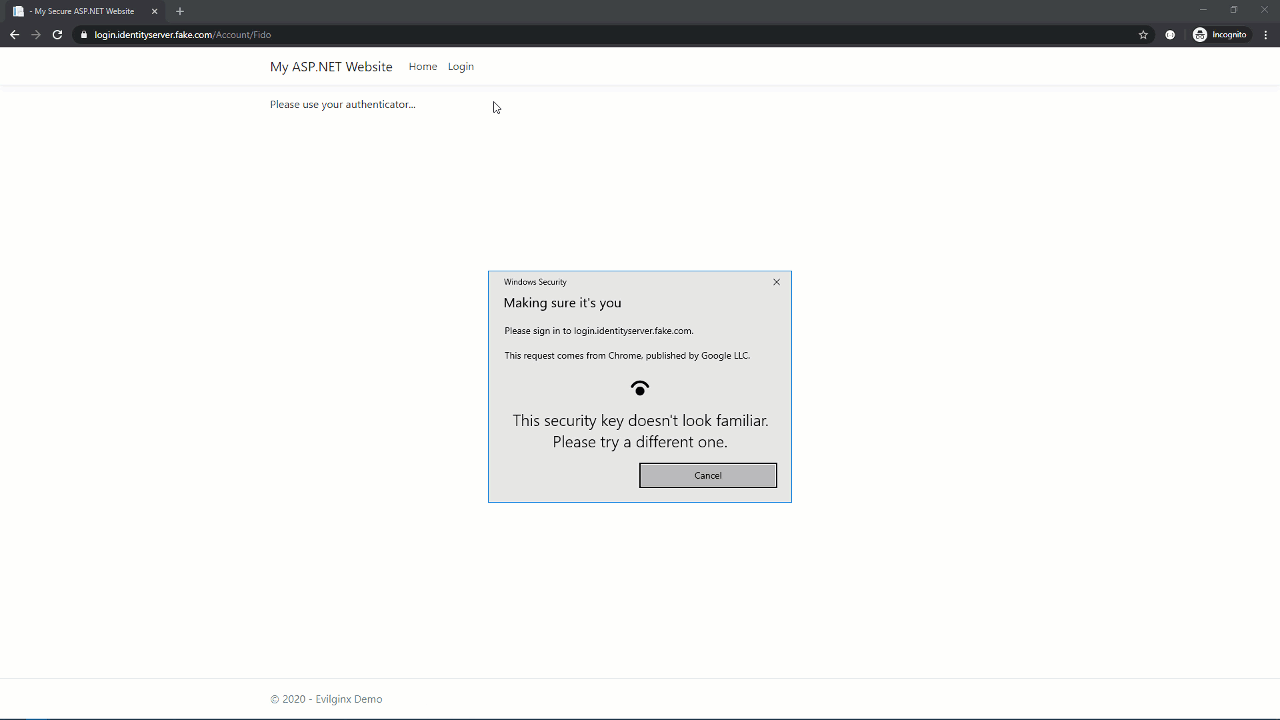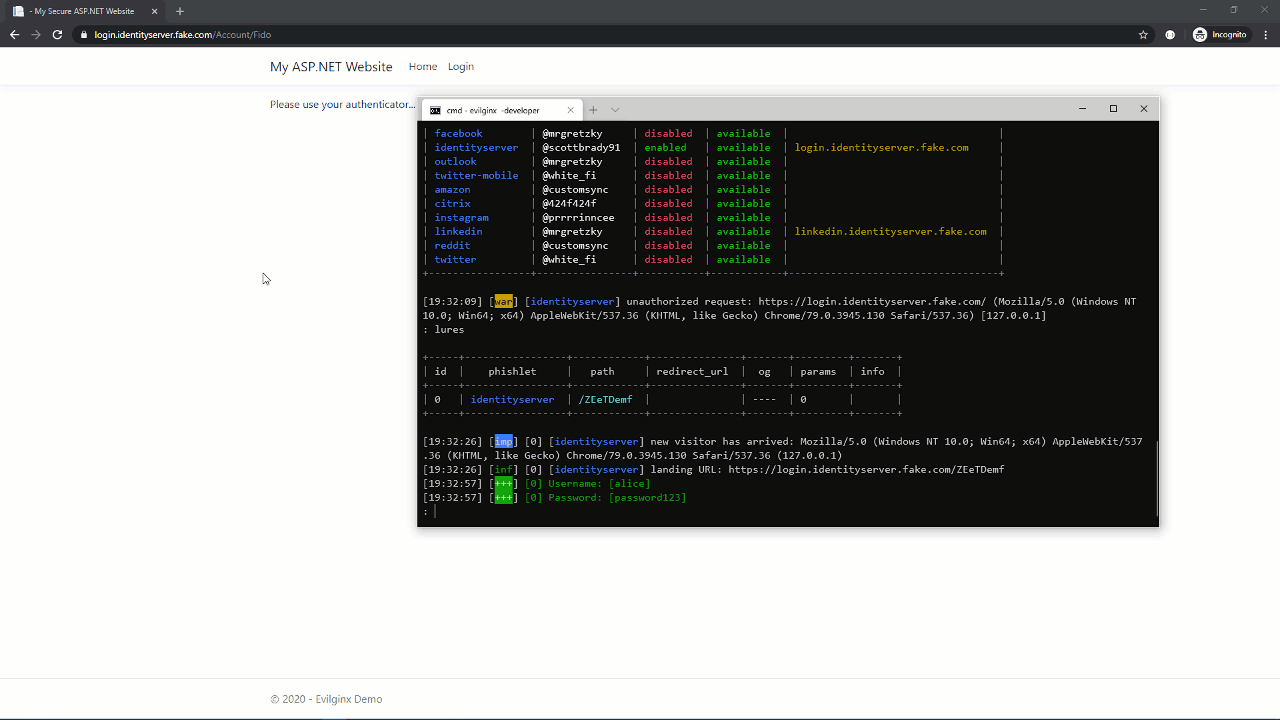
This time, it didn’t work. The target site still challenged the user for their second factor and even requested the same credential. WebAuthn sent this credential ID to the user’s FIDO authenticator, but it also sent the domain in the browser’s address bar, and since FIDO credentials are coupled to a domain, it simply won’t work.
Evilginx still saw the user’s username and password, but because the FIDO authenticator refused the authentication request, it failed to steal a session cookie.
FIDO2 for ASP.NET Core
This example used Rock Solid Knowledge’s FIDO component running in an ASP.NET Core website. This component’s design focusses on make FIDO as easy as possible for developers to integrate into their ASP.NET Core application; as a result, the server-side code for this implementation amounted to roughly six lines of code.
Evilginx is an amazingly simple tool to use; it handles the networking for you and will even automatically generate a Let’s Encrypt TLS certificate for your phishing domain. Phishing is now one of the biggest threats to your user’s and tools such as Evilginx and Modlishka show just how simple it is to implement sophisticated phishing attacks. Only standards such as WebAuthn and FIDO2 offer the protection you need.

